Table of Contents
Prerequisite Terminology
Before diving into the TLS Handshake Steps: Encryption, Authentication, and Security process, it’s essential to understand some key terms:
Client (Browser): The client is the entity that initiates a connection to a server, typically a web browser in the context of HTTPS connections. It requests resources from the server and receives responses.
Server: The server is the entity that hosts resources or services and responds to client requests. It provides data or services to the client and ensures secure communication through protocols like TLS.
Certificate Authority (CA): A CA is a trusted entity responsible for issuing digital certificates. These certificates authenticate the identity of organizations or individuals and contain the public keys used in asymmetric encryption.
Premaster Secret: The premaster secret is a randomly generated value created by the client during the TLS handshake. It is encrypted with the server’s public key and sent to the server to establish a secure communication channel.
Public Key: A public key is part of asymmetric encryption. It is used to encrypt data and can be shared openly. In the TLS handshake, the server’s public key is used to encrypt the premaster secret.
Private Key: The private key is the counterpart to the public key in asymmetric encryption. It is kept secret by the owner and is used to decrypt data encrypted with the corresponding public key. The server uses its private key to decrypt the premaster secret.
Authentication: Authentication is the process of verifying the identity of a party in a communication. In TLS, server authentication is achieved using the server’s digital certificate issued by a CA.
Integrity: Integrity ensures that data has not been altered during transmission. In TLS, integrity is maintained through cryptographic hash functions and Message Authentication Codes (MACs) included in the handshake messages.
Confidentiality: Confidentiality ensures that data is not accessible to unauthorized parties. In TLS, confidentiality is achieved through encryption, both asymmetric (for the premaster secret) and symmetric (for the session data).
Understanding 3 TLS Handshake Steps: Encryption, Authentication & Security
The Transport Layer Security ,TLS handshake steps are critical processes in establishing a secure communication channel between a client (e.g., a web browser) and a server. This article explores the steps involved in the TLS handshake steps, focusing on the three fundamentals: encryption, authentication, and security.
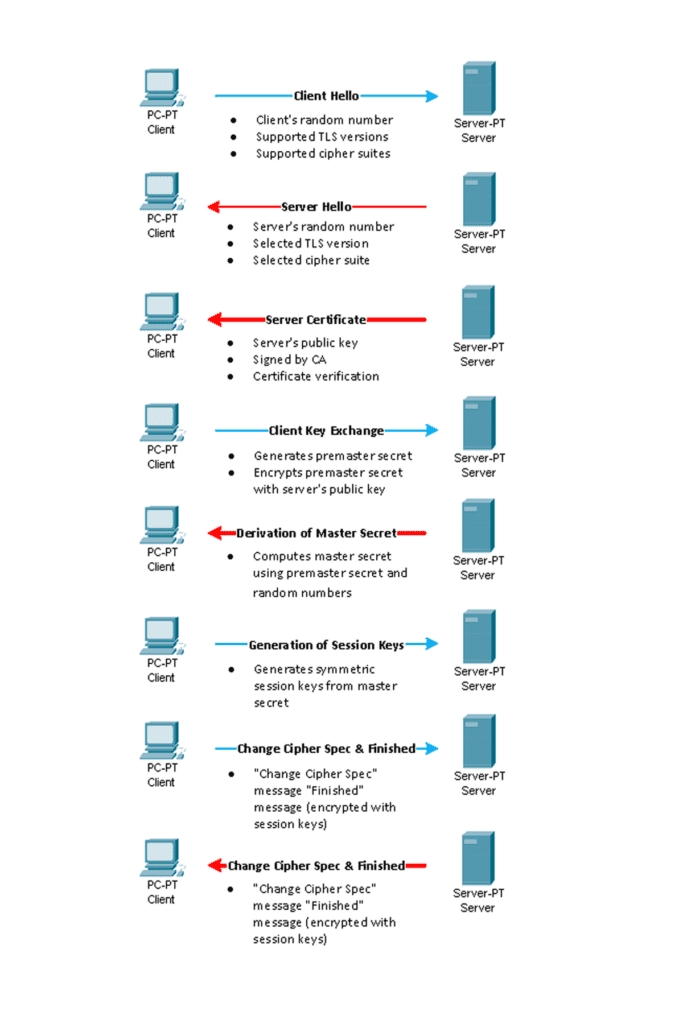
1. Client Hello
Process: The client initiates one of the first TLS handshake steps by sending a “Client Hello” message to the server. This step begins the negotiation of the secure connection.
Content: The “Client Hello” message includes:
- The client’s random number: A unique value generated by the client to ensure the security of the session.
- Supported TLS versions: The versions of the TLS protocol that the client supports.
- Cipher suites: The cryptographic algorithms supported by the client, including those for encryption and hashing.
Encryption Method: None (unencrypted initial message).
Authentication: None (initial message does not authenticate the client).
Integrity: None (initial message does not include mechanisms to ensure data integrity).
Confidentiality: None (initial message is sent in plaintext).
The “Client Hello” message sets the stage for the secure communication by indicating the client’s capabilities and preferences for the TLS connection.
2. Server Hello
Process: The server responds with a “Server Hello” message. This message acknowledges the client’s request and provides the necessary information for the continuation of the TLS handshake steps.
Content: The “Server Hello” message includes:
- The server’s random number: A unique value generated by the server for the session.
- Selected TLS version: The version of TLS chosen by the server from the client’s list of supported versions.
- Cipher suite: The cryptographic algorithms chosen by the server from the client’s list of supported cipher suites.
Encryption Method: None (unencrypted response).
Authentication: None (initial response does not authenticate the server).
Integrity: None (initial response does not include mechanisms to ensure data integrity).
Confidentiality: None (initial response is sent in plaintext).
The “Server Hello” message confirms the TLS version and cipher suite that will be used, as well as providing the server’s random number for further steps in the handshake.
3. Server Certificate
Process: The server sends its digital certificate to the client. This certificate is crucial for establishing the server’s identity and is used in the authentication process.
Content: The server’s digital certificate contains:
- The server’s public key: Used by the client to encrypt the premaster secret.
- The certificate authority’s (CA) signature: A digital signature from the CA that issued the certificate, which verifies its authenticity.
Encryption Method: None (the certificate is sent in plaintext).
Authentication: Server authentication is achieved through the certificate issued by a CA. The client verifies the server’s identity by checking the CA’s signature on the certificate.
Integrity: Provided by the CA’s digital signature, which ensures that the certificate has not been tampered with.
Confidentiality: None (the certificate is not encrypted and is sent in plaintext).
The server certificate provides the client with the server’s public key and allows the client to authenticate the server’s identity using the CA’s signature.
4. Client Key Exchange
Process: The client generates a premaster secret, encrypts it using the server’s public key, and sends it to the server. This step establishes a shared secret between the client and server that will be used to generate session keys.
Content: The premaster secret is a random value generated by the client and is encrypted with the server’s public key to ensure that only the server can decrypt it.
Encryption Method: Asymmetric encryption (the premaster secret is encrypted using the server’s public key).
Authentication: Implicit authentication occurs as the client uses the server’s public key for encryption, confirming the server’s identity.
Integrity: Provided by the encryption and decryption processes, which ensure that the premaster secret is securely transmitted.
Confidentiality: Ensured by asymmetric encryption, which prevents unauthorized parties from accessing the premaster secret.
The client key exchange step is critical for establishing a secure communication channel, as it securely transmits the premaster secret to the server.
5. Derivation of Master Secret
Process: Both the client and server use the premaster secret, along with their respective random numbers, to compute the master secret. This master secret is then used to generate session keys.
Content: The master secret is derived locally by both parties using the premaster secret and random numbers exchanged during the handshake.
Encryption Method: None (local computation).
Authentication: None (local computation).
Integrity: None (local computation).
Confidentiality: None (local computation).
The master secret is used to derive symmetric session keys for encrypting the data exchanged during the session. This step ensures that both the client and server have the same session keys.
6. Generation of Session Keys
Process: The master secret is used to generate symmetric session keys for encrypting and decrypting data during the TLS session.
Content: Symmetric keys are created for encrypting the data exchanged between the client and server.
Encryption Method: None (local computation).
Authentication: None (local computation).
Integrity: None (local computation).
Confidentiality: None (local computation).
Session keys are used for symmetric encryption of data, ensuring that communication between the client and server is secure. These keys are derived from the master secret and are used for the rest of the session.
7. Change Cipher Spec and Finished (Client)
Process: The client sends a “Change Cipher Spec” message, followed by a “Finished” message. The “Change Cipher Spec” message indicates that subsequent messages will be encrypted using the negotiated cipher suite. The “Finished” message is encrypted with the session keys.
Content:
- “Change Cipher Spec” message: Indicates that the client will now use the negotiated cipher suite for encryption.
- “Finished” message: Contains a hash of all previous handshake messages and is encrypted using the session keys.
Encryption Method: Symmetric encryption (for the “Finished” message).
Authentication: Implicit authentication is achieved as the “Finished” message includes a hash of all previous handshake messages, confirming the integrity of the handshake.
Integrity: Provided by the Message Authentication Code (MAC) included in the “Finished” message.
Confidentiality: Ensured by symmetric encryption of the “Finished” message.
The “Change Cipher Spec” and “Finished” messages finalize the handshake process from the client’s side, ensuring that future communications are encrypted and secure.
8. Change Cipher Spec and Finished (Server)
Process: The server sends a “Change Cipher Spec” message, followed by a “Finished” message. Similar to the client, the “Change Cipher Spec” message indicates that the server will now use the negotiated cipher suite for encryption. The “Finished” message is encrypted with the session keys.
Content:
- “Change Cipher Spec” message: Indicates that the server will use the negotiated cipher suite for subsequent messages.
- “Finished” message: Contains a hash of all previous TLS handshake steps messages and is encrypted using the session keys.
Encryption Method: Symmetric encryption (for the “Finished” message).
Authentication: Implicit authentication is achieved as the “Finished” message includes a hash of all previous handshake messages, confirming the integrity of the handshake.
Integrity: Provided by the MAC included in the “Finished” message.
Confidentiality: Ensured by symmetric encryption of the “Finished” message.
The “Change Cipher Spec” and “Finished” messages complete the TLS handshake steps from the server’s side, ensuring that both parties are now using the agreed-upon encryption methods for secure communication.
Conclusion
Understanding the TLS handshake steps is a fundamental aspect of securing online communications. By understanding the steps involved—Client Hello, Server Hello, Server Certificate, Client Key Exchange, Derivation of Master Secret, Generation of Session Keys, and Change Cipher Spec and Finished messages—you can appreciate how 3 fundamental TLS handshake steps ensures encryption, authentication, and security.
Encryption is achieved through both asymmetric and symmetric methods during the handshake, providing a secure channel for data transmission. Authentication is established via digital certificates and the verification of the server’s identity. Security is maintained through a combination of encryption, integrity checks, and confidentiality measures, ensuring that data remains protected from unauthorized access.
For a deeper dive into the TLS handshake steps and its cryptographic principles, you can refer to the following sources:
References
Barkan, E. B. (2007). TLS Handshake and Cryptographic Protocols. Springer.
Dierks, T., & Rescorla, E. (2008). The Transport Layer Security (TLS) Protocol Version 1.2. RFC 5246. https://tools.ietf.org/html/rfc5246
Katz, J., & Lindell, Y. (2007). Introduction to Modern Cryptography: Principles and Protocols. Chapman & Hall/CRC.